Coronavirus, COVID-19, has permeated throughout the world affecting millions. The pandemic has caused a serious impact not only on people’s daily lives and economic development of entire countries but also on international trade and businesses in general. Various governments have developed contact tracing apps as a preventive measure. It is thought to be an essential public health tool for controlling infectious disease outbreaks. This app helps track the chain of contact and notifies its users when they have come in contact with infected individuals or are in danger of contracting this virus. The German Government’s tool – Corona-Warn-App (CWA), is now open source and we took this opportunity to analyse it.
We scanned the backend component of CWA via Embold’s Static Analysis platform and did a quick run-through of the findings.
Component scanned: cwa-server (https://github.com/corona-warn-app/cwa-server.git)
Commit ID: 822150b1b22645ba071a6f6576d50614dc01b34b
Implementation language: Java
Overview
First off, the system quality looks good from an overall perspective. Embold analyses systems from 4 dimensions
- Design Quality,
- Code Quality,
- Implementation Metrics, and
- Code Duplication.
The issues found in each of these dimensions are hashed into an overall rating on a scale from -5 to + 5 and this score is assigned to every code component (class, module, system, etc.). This then becomes the Embold Score (on a scale of -5 to +5) at a system level.
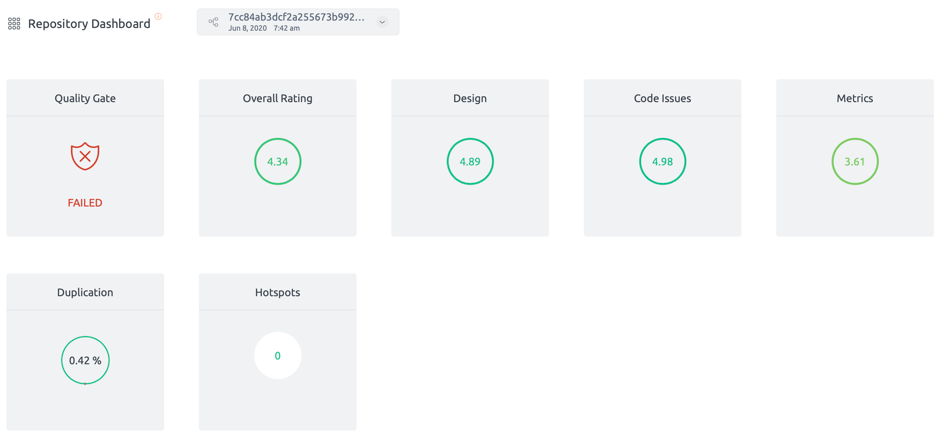
System Overview
- Overall Rating:
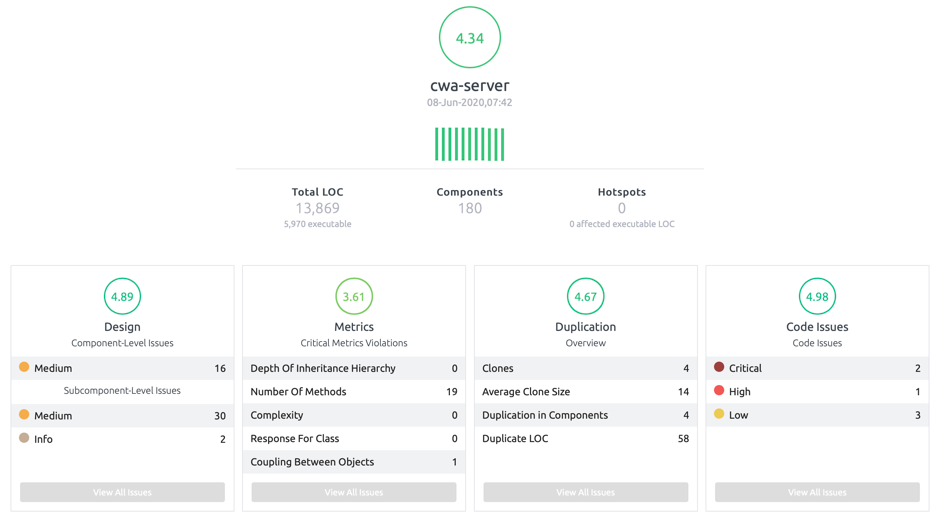
The overall Embold score of the cwa-server is a healthy 4.34.
The individual scores (including design, metrics, duplication, and code issues) are also good, and no hotspots were detected.
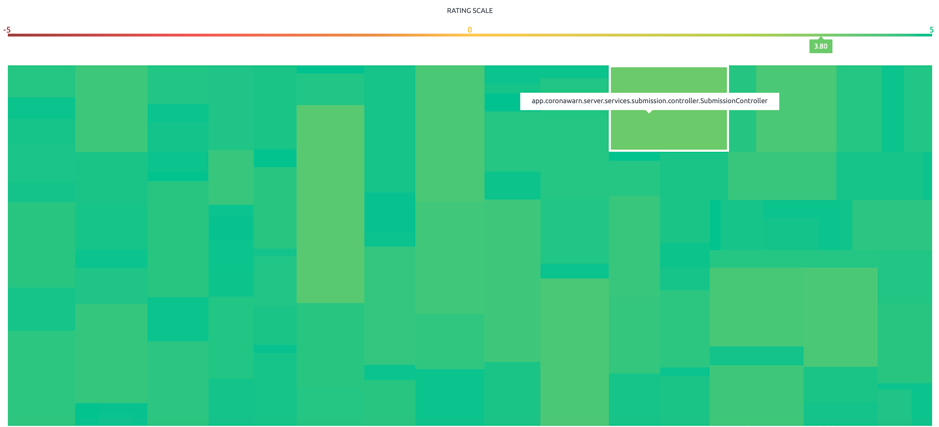
The same is reflected in the system heatmap (class SubmissionController, although not a hotspot, is a relatively large class in the system)
However, the Quality Gate of the system failed due to 2 critical code issues. These may impact the security and resource utilization of the system.
Code Issues:
This section lists the critical code issues detected.
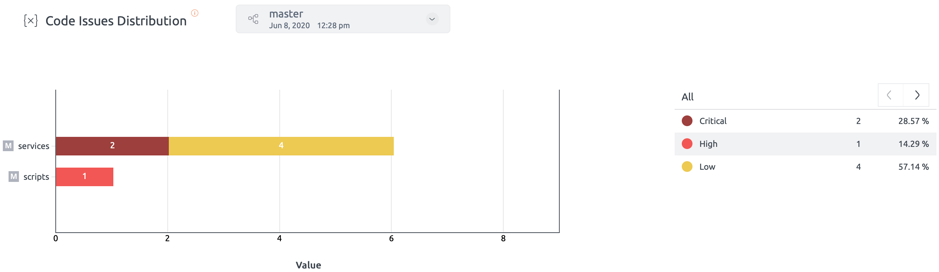
We found two critical issues
Let’s examine these in detail:
- DisabledSpringSecurityCSRF:
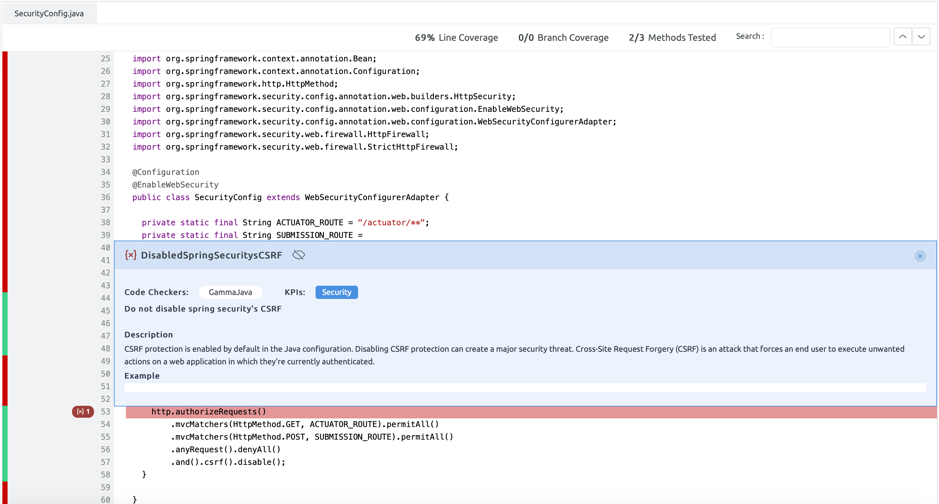
Class app.coronawarn.server.services.submission.config.SecurityConfig disables csrf in the configure() method, which can potentially make it possible to introduce a CSRF attack. Our recommendation is to not disable it, as Spring Security enables it by default. But In the CWA use case, authentication or sessions are not applied, so this may not present a real threat, but nonetheless we recommend CSRF is not disabled.
- PossibleThreadLeakInExecutorService:
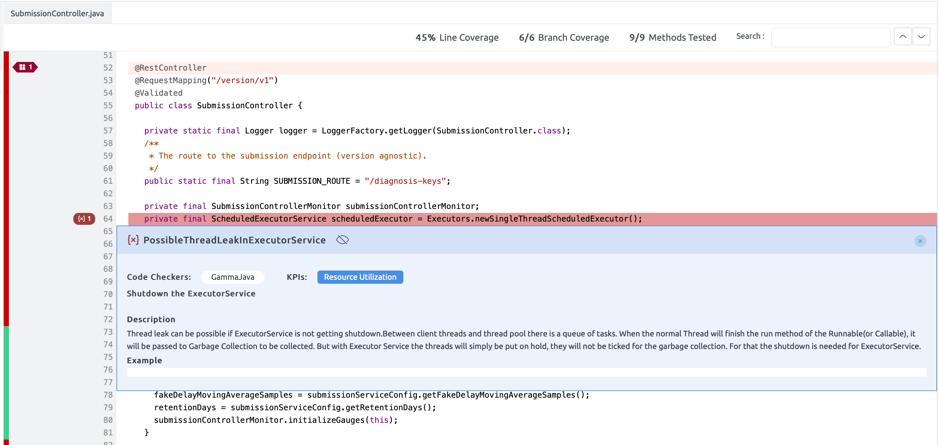
Class SubmissionController creates a scheduledExecutor of the ScheduledExecutorService. It is important to call shutdown() or shutdownNow() of the ScheduledExecutorService at shutdown or when it is no longer needed. The class SubmissionController does not call the shutdown() or shutdownNow() methods, leading to a resource leak. Our recommendation is to make sure the shutdown() happens gracefully via a shutdown callback or other equivalent approach to ensure no resource leak happens. This issue was discussed here: https://github.com/corona-warn-app/cwa-server/issues/433 and although the SubmissionController is a singleton in this case (and hence the issue was not fixed), we do recommend it should shut down the ScheduledExecutorService during app exit.
Design Analysis:
In its current state, no major design anti-patterns were found. However, we recommend the following classes should be observed over time as they may turn into God Classes when more functionality is added.
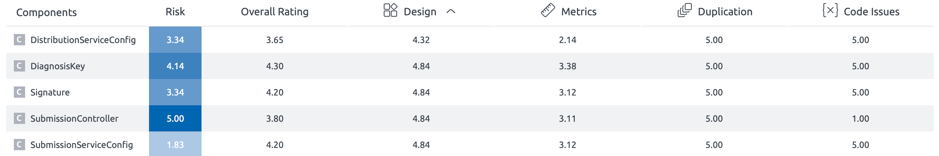
These classes have a relatively low metrics score (that means more lines of code, functionality, abstractions represented here). As new logic is added over time, they may start showing traits such as lack of separation of concerns, many dependencies, etc. and may start getting difficult to maintain and become defect prone. Hence, we recommend that these classes should be monitored.
For more information, you can refer to our website here at www.embold.io and documentation at docs.embold.io.


Comments are closed.